Soldering Assignment
Description
The soldering assignment is a basic soldering exercise that ensures all ECE 445/ME 470 students understand how to solder surface-mount and through-hole devices. Students will be provided with the necessary PCB, components, solder, flux, etc. The details of the soldering assignment can be found in the assignment sheet.
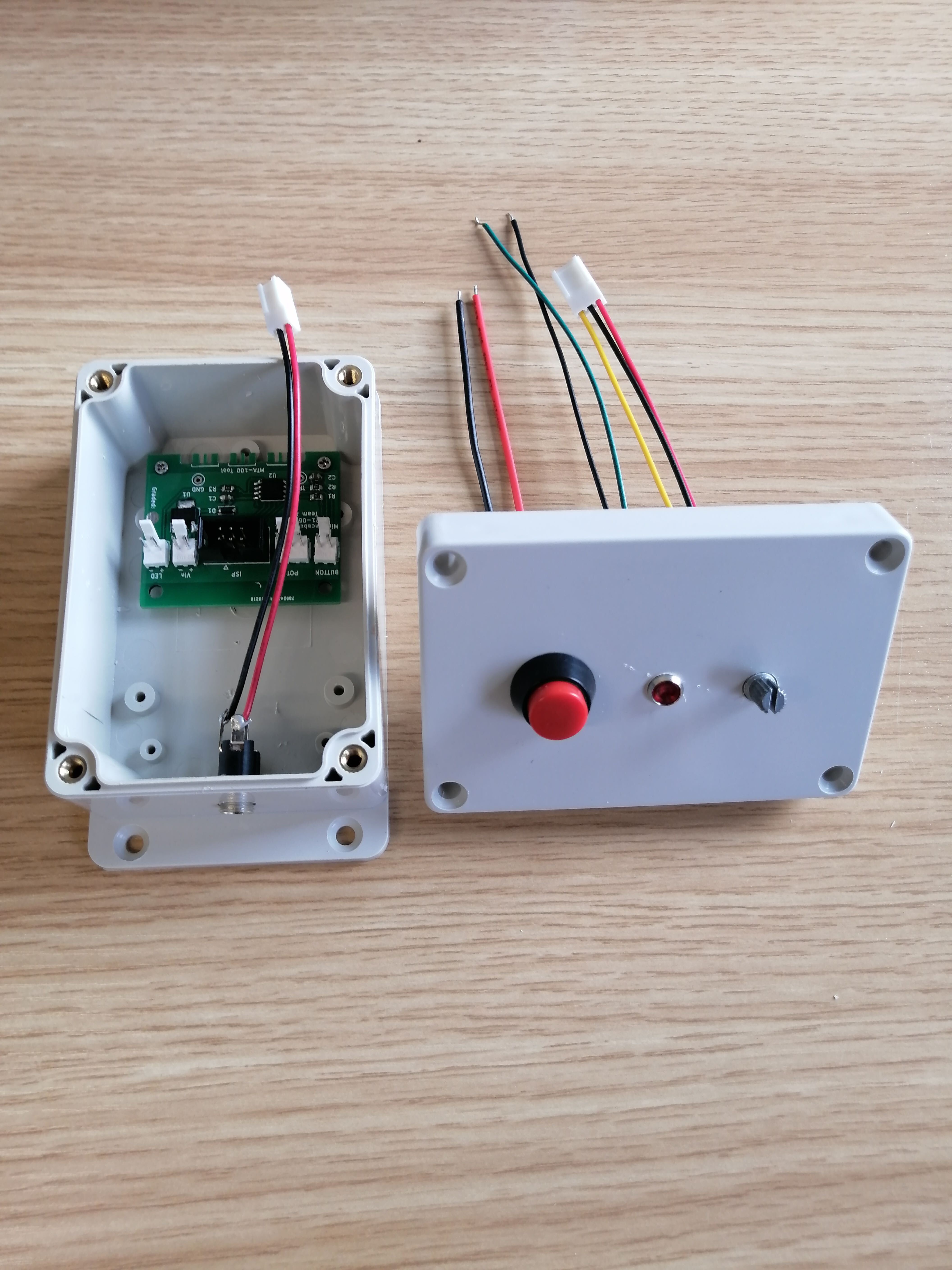
Your end product should look similar to the following. You will create a small device that blinks an LED at varying frequencies when the button is pressed, based on a potentiometer reading.
Below is a series of soldering tutorials. The critical ingredient that you need to make your life easier while surface mount soldering (and through-hole too) is flux. There is liquid, water-soluble flux available in the lab. If you can't find it or don't know what it looks like, ask a lab staff member or TA for help.
Requirements and Grading
The soldering assignment is worth 10 points and is graded via inspection by a TA or Lab Staff member. Students are allowed to make as many attempts as necessary to complete the assignment.
Submission and Deadlines
The soldered PCB must be presented to a course staff member before the deadline listed on the Course Calendar.
Video Tutorials
Below are a few public video tutorials on Soldering. There is also a text description of how to solder on the soldering assignment doc linked above.Through-hole (THT) and surface-mount (SMD) soldering tutorial:
Tutorial on using the various types of flux:
Tutorial on using wick to remove solder:
Tutorial on using a heat gun: